Modern applications rely on multiple technologies working together – web servers, frameworks, proxies, and libraries – all interpreting input in their own way. When these parsers process the same data differently, inconsistencies appear that can turn into exploitable security gaps.
Parser differential vulnerabilities arise from these inconsistencies. Attackers can craft inputs that look harmless to one component but are handled differently by another, bypassing validation or triggering unintended actions. The result can range from input filtering bypasses to unauthorized access or even remote code execution.
During penetration testing for our clients, Iterasec specialists often uncover parser differential vulnerabilities in complex systems where automated scanners show no findings. Detecting such issues requires understanding how different parsers behave under edge cases and how their interactions can lead to unexpected results.
This article explains what parser differential vulnerabilities are, how they affect security, why they’re hard to detect automatically, and what can be done to prevent them.
What Are Parser Differential Vulnerabilities
Parser differential vulnerabilities pose a critical threat to modern applications and infrastructures that rely on multiple technologies to process data. They occur when different parsers interpret the same input in inconsistent ways, creating exploitable gaps that attackers can manipulate to bypass security controls.
Such vulnerabilities typically arise because various components, like web servers, application frameworks, or middleware, use different parsing engines to handle the same input data. These engines may differ in how they process special characters, encoding, or duplicated and malformed structures. Attackers can craft inputs that appear safe to one parser but are treated as malicious by another, effectively bypassing validation, filtering, or access restrictions.
This inconsistency can lead to several types of security issues, including:
- Input validation bypass – malicious payloads slip through sanitization filters.
- Unauthorized access – differences in interpretation allow bypassing authentication or authorization checks.
- Remote code execution – certain parsers may execute injected code due to improper handling of input.
Detecting and mitigating parser differential vulnerabilities is challenging. It often requires a deep understanding of multiple parsing engines and their edge-case behaviors. Modern software stacks typically combine components written in different languages and libraries, making it easy for inconsistencies to appear unintentionally.
To minimize risks, it’s essential to ensure consistent parsing across all components or to validate data as close as possible to the point of execution. Doing so helps prevent discrepancies that attackers can exploit.
Manual testing plays a crucial role in uncovering parser differential vulnerabilities. Automated tools alone cannot fully capture the nuanced inconsistencies that occur when different parsers interpret the same data differently. These subtle differences are often invisible to scanners, which rely on predefined patterns and signatures. Manual testing allows security experts to simulate realistic attack scenarios, analyze parser behavior contextually, and identify cases where minor variations lead to exploitable flaws.
This hands-on approach ensures deeper validation and helps prevent bypasses or misinterpretations that could compromise systems relying on parser outputs. By combining human expertise with targeted fuzzing and analysis, teams can identify vulnerabilities that automated tools consistently overlook.
Real-World Cases of Parser Differential Vulnerabilities
Parser differential vulnerabilities are increasingly common in web applications that involve middleware components such as proxies, cache servers, and web application firewalls, as well as in microservice architectures.
HTTP Request Smuggling
A well-known type of parser differential vulnerability is HTTP request smuggling. This vulnerability exploits inconsistencies in HTTP request parsing between front-end servers (e.g., proxies, load balancers) and back-end servers. These inconsistencies occur because the HTTP/1.1 protocol allows two ways to delimit request bodies: the Content-Length header and the Transfer-Encoding header.
When these headers are present ambiguously, different servers might interpret the request boundaries differently, leading to vulnerabilities. HTTP request smuggling is a classic parser differential vulnerability that has affected many widely used web servers and proxy architectures. Differential fuzzing and crafted request payloads remain essential techniques for discovering and confirming these vulnerabilities in penetration tests.
URL Parser Differential Vulnerabilities
A URL parser differential vulnerability arises when different components in an application interpret the same URL string inconsistently due to variations in the URL parsing logic or standards they implement. Over the years, many RFCs have defined URLs, and different parsers may adhere to different and sometimes outdated specifications. The W3C/WHATWG standard and RFC 3986 are two notable variations.
An example of such a vulnerability is the Open Redirect in mod_auth_openidc, identified as CVE-2021-32786. The Apache2 module mod_auth_openidc, which handles authentication flows, uses the apr_uri_parse function based on RFC 3986, while modern web browsers follow the WHATWG living standard for URL parsing. This leads to an inconsistency where certain characters such as backslashes are interpreted differently: browsers may treat a backslash as a path delimiter, while the apr_uri_parse function treats it as part of a userinfo section of the URL.
Consequently, mod_auth_openidc might validate a URL as safe because it sees the host as expected, but the browser’s interpretation results in redirection to a completely different domain. Attackers can exploit this mismatch to bypass security checks such as open redirect protections, potentially leading to phishing attacks that leverage user trust in a legitimate domain.
Such inconsistencies are difficult to detect because they depend on nuanced differences in URL standards and implementations between client-side and server-side components. Addressing these vulnerabilities often requires aligning parser behavior or implementing mitigations such as normalizing problematic characters before parsing. This example shows that libraries may follow different standards describing the same technology.
TARmaggedon Vulnerability (CVE-2025-62518)
Another recent example of a parser differential vulnerability caused by the diversity of standards is the TARmaggedon vulnerability (CVE-2025-62518) in the popular async-tar Rust library and its forks, including the widely used tokio-tar crate. This issue impacts major projects such as uv (Python package manager), testcontainers, and wasmCloud.
This vulnerability is a desynchronization flaw that allows an attacker to “smuggle” additional archive entries into TAR extractions. It occurs when processing nested TAR files that contain a file-size mismatch between their PAX extended headers and ustar headers. When handling archives with PAX-extended headers specifying overridden sizes, the parser incorrectly advances the stream position based on the ustar header size (often zero) instead of the PAX-specified size. As a result, it interprets parts of file content as legitimate TAR headers.
Beyond the lack of file-size validation, the deeper cause lies in the diversity of partially compatible TAR formats, which introduces significant complexity in TAR archive parsers.
ZIP Archive Parsing and Signature Verification
There are also less-known examples of parser differential vulnerabilities that lead to serious security impact for applications. One common case involves improper parsing of ZIP archives containing signed update packages. Inconsistencies in locating the Central Directory of a ZIP archive can lead to signature verification bypasses.
A critical example is the signature verification bypass in Huawei recovery mode, identified as CVE-2021-40045. This vulnerability allows attackers to apply unauthentic firmware updates and achieve arbitrary code execution in recovery mode, enabling full control over the device at a low level. The root cause lies in how Huawei implements update.zip files – ZIP archives containing update data with an appended signature in the ZIP comment section.
The vulnerability exploits inconsistencies in the End of Central Directory (EOCD) handling between the signature verification code and the ZIP extraction code (minzip). The verification process relies on a footer that defines the EOCD and signature size, but this footer itself is not signed. Attackers can inject additional data or even a secondary ZIP archive between the EOCD and the signature. As a result, the verifier checks the original signed archive, while the extractor processes the injected archive, allowing tampered update contents to bypass cryptographic verification.
This case demonstrates the dangers of parser and implementation inconsistencies in security-critical components and emphasizes the importance of thorough, end-to-end validation and secure signature verification in update infrastructures.
CRX3 File Signature Verification Bypass
Another example of such a vulnerability is the CRX3 File Signature Verification Bypass via Embedded ZIP64 Payload in Chromium, titled CVE-2024-0333. An attacker could craft a CRX3 file embedding a ZIP64 payload in a way that the signature verification parser interprets the archive differently from the Minizip extraction parser.
This vulnerability enables an attacker to bypass signature verification by embedding malicious payloads that are not detected during integrity checks but are processed and executed once extracted. Essentially, the signature check approves a legitimate-looking CRX3 file, while the embedded ZIP64 payload contains unauthorized content. During the Chromium extension installation, Minizip locates and extracts the attacker-controlled, unsigned ZIP64 payload instead of the intended signed payload.
These examples demonstrate a core risk in systems that process structured data through multiple parsers: when different components analyze the same input at different stages – verification, extraction, or installation – any discrepancy in interpretation can be exploited to bypass security controls. Such vulnerabilities are especially dangerous in software update mechanisms, where maintaining package integrity and authenticity is critical for system security.
Case Study: Parser Differentials in Recent Engagement
During a recent penetration testing engagement, Iterasec identified a parser differential vulnerability in a license signature verification procedure that allowed an attacker to modify license properties without invalidating the digital signature. Another parser differential vulnerability in certificate authentication allowed an unauthenticated attacker to impersonate any user.
JSON Signature Verification Bypass
The license file consisted of a JSON object containing two elements: a properties object and a signature string with an RSA digital signature of the properties contents. The target Python application used different parsing methods during the signature verification and the license properties parsing processes.
During signature verification, the application read the license file as a string and located the properties object using the str.find function. For property parsing, it used the json.loads function. This approach created a security issue when the license file contained duplicated properties objects.
The following simplified Python script illustrates the behavior:
import json
def extract_properties(license: str) -> str:
return license[
license.find('{', license.find('"properties": ')) : license.find('}') + 1
]
def parse_properties(license: str) -> dict:
return json.loads(license)['properties']
license = '{"properties": {"end_date": "2000-01-01", "note": "Original license properties"}, "signature": "..."}'
properties = extract_properties(license)
print(f"License verification stage:\n{properties!r}\n")
# Signature verification with extracted properties object ...
properties = parse_properties(license)
print(f"License properties parsing after verification:\n{properties!r}\n")
With a valid license, both parsing methods produce consistent results:
License verification stage:
'{"end_date": "2000-01-01", "note": "Original license properties"}'
License properties parsing after verification:
{'end_date': '2000-01-01', 'note': 'Original license properties'}
However, if the license file contains duplicated properties objects, it’s possible to mislead the parser and alter license properties while keeping the original signature valid.
Since the str.find function returns the first match in a string, it extracts and verifies the first properties object. The json.loads function, however, reads the second duplicated object. This inconsistency means the application verifies the digital signature of one object but later uses a different one during runtime.
A forged license example (duplicated object is highlighted in red color):
{"properties": {"end_date": "2000-01-01", "note": "Original license properties"}, "signature": "...", "properties": {"end_date": "2099-12-31", "note": "License properties are modified by an attacker"}}
Python script output:
License verification stage:
'{"end_date": "2000-01-01", "note": "Original license properties"}'
License properties parsing after verification:
{'end_date': '2099-12-31', 'note': 'License properties are modified by an attacker'}
Certificate Authentication Bypass
The application used certificate-based authentication for REST API users. Each client provided its certificate in an HTTP header, which the application validated against CA certificates issued by the system administrator. After successful verification, the application extracted the subject’s Common Name (CN) field to determine the username. The validation was performed using the openssl verify OS command, while certificate parsing relied on the cryptography Python module.
As Iterasec performed differential fuzzing to identify potential inconsistencies in PEM-encoded certificate parsing, testing revealed that OpenSSL strictly required certificates to start with a valid PEM header, whereas the cryptography parser accepted extra characters before it. Although the cryptography module uses OpenSSL as its backend for cryptographic operations, it implements its own certificate parser with slightly different input-handling logic.
Additionally, the lack of HTTP header validation allowed an attacker to supply multiple certificates in a single request.
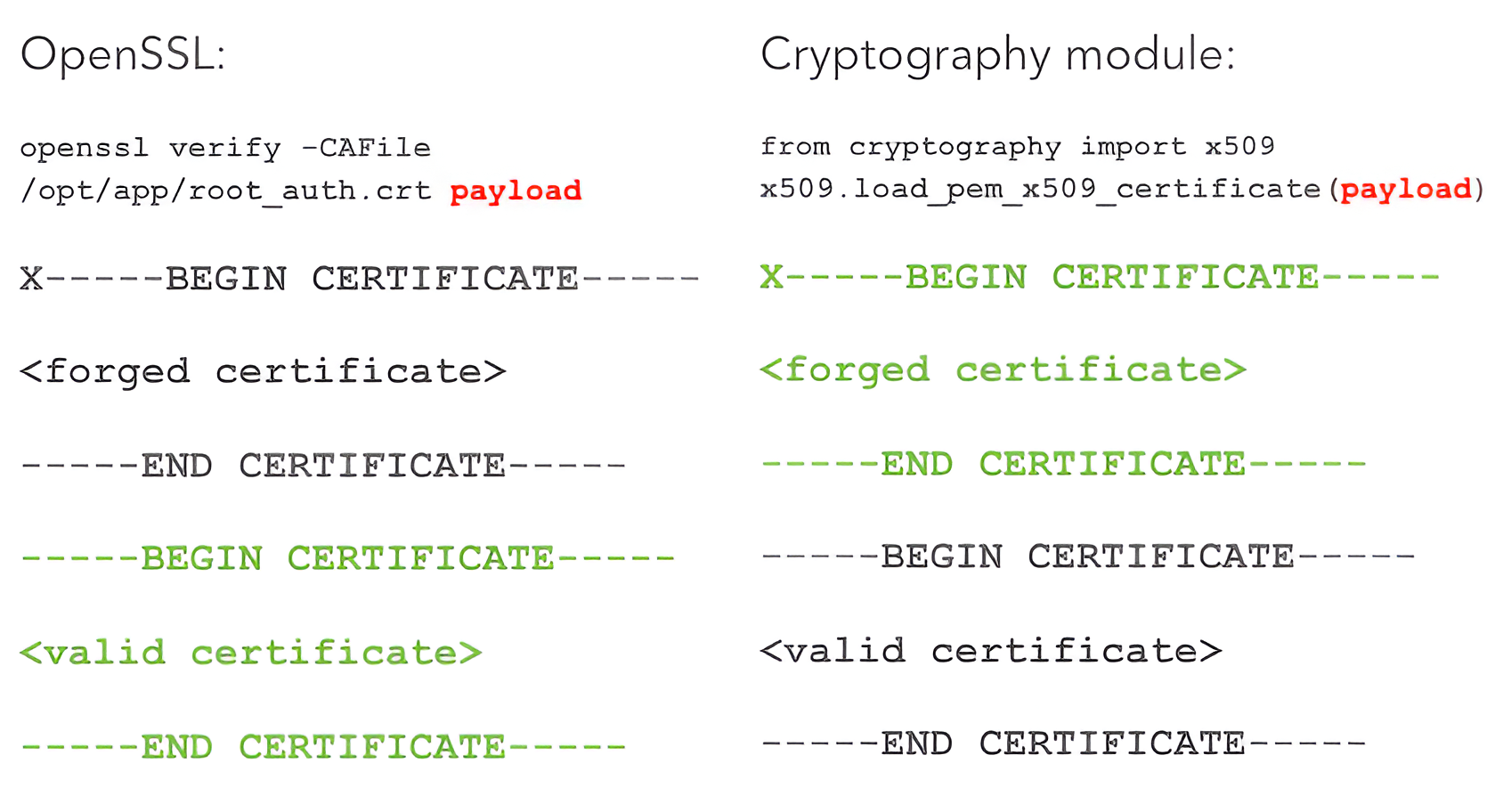
By combining these issues, Iterasec was able to mislead the certificate parser during the verification stage, causing the application to accept and parse an untrusted duplicated certificate.
Practical Mitigation Tips for Parser Differential Vulnerabilities
Parser differential vulnerabilities are complex, but their impact can be significantly reduced with disciplined design and consistent validation practices. Preventing inconsistencies requires both technical alignment between components and a thorough security testing strategy.
To strengthen protection against parser differential issues, organizations should:
- Standardize parsers across layers.
Use the same parsing libraries or engines throughout the technology stack whenever possible to ensure consistent input handling. - Implement strong input normalization.
Normalize input data into a canonical form before validation and processing to minimize the risk of inconsistent interpretations. - Configure strict parsing modes.
Disable unnecessary parser features that may introduce ambiguity or unexpected behavior. - Adopt defense-in-depth.
Combine client-side and server-side validation so that any bypass at one layer can be caught by another. - Conduct comprehensive multi-parser testing.
Test critical inputs against all parsers involved in data processing to identify inconsistencies early. - Integrate automated fuzzing tools.
Use fuzzing frameworks that generate diverse and edge-case inputs to uncover parser-specific vulnerabilities. - Keep parsers updated.
Regularly apply security patches and updates to parsing libraries and frameworks to mitigate known vulnerabilities.
At Iterasec, our penetration testing specialists uncover these subtle flaws that often remain invisible to automated scanners. We apply a combination of techniques to identify and mitigate parser differential vulnerabilities, including:
- Cross-parser analysis – testing how different parsers handle the same input to detect inconsistencies.
- Input fuzzing – generating a broad range of test cases to reveal unexpected parser behavior.
- Security control validation – ensuring consistent enforcement of validation and filtering rules across all layers.
- Custom payload crafting – simulating real-world attack scenarios that expose parser differential weaknesses.
Effective mitigation starts with understanding how each component interprets input. Consistent parsing, comprehensive testing, and expert manual analysis together form the foundation of resilient application security.
Conclusion
Parser differential vulnerabilities represent one of the more subtle and overlooked risks in modern application security. They arise from inconsistencies between components that interpret the same data differently, creating conditions that traditional scanners often fail to detect.
Because these vulnerabilities exist at the intersection of design, implementation, and real-world behavior, addressing them requires more than static checks or automated testing. Consistent parsing across components, proper input normalization, and manual dynamic analysis remain the most effective defenses.
Through detailed penetration testing, Iterasec helps organizations identify and eliminate these inconsistencies before they can be exploited. Understanding how different parsers interact and ensuring they interpret data in a predictable, uniform way is key to maintaining the integrity and security of complex systems.
Need to assess your systems for hidden parser differential vulnerabilities? Reach out to the Iterasec penetration testing team to ensure your applications are resilient against complex, parser-driven attacks.

![Understanding How Attackers Exploit HTTP Redirects in Web Applications [Part 1]](https://iterasec.com/wp-content/uploads/2024/06/Same-Origin-Policy-768x528.jpg)
![Understanding How Attackers Exploit HTTP Redirects in Web Applications [Part 2]](https://iterasec.com/wp-content/uploads/2024/08/JavaScript-Based-HTTP-Redirect-Exploits-1-768x439.jpeg)
