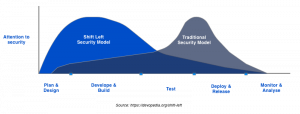
Why IoT Penetration Testing Services are Important
IoT penetration testing services are vital for safeguarding your IoT ecosystem. Here’s why they are indispensable:
Uncover Hidden Vulnerabilities
IoT devices often have unique security challenges that aren't apparent through standard security assessments. Penetration testing reveals these hidden weaknesses before they can be exploited.
Validate Existing Security Measures
Penetration testing allows you to test the effectiveness of your current security controls against real-world attack scenarios, ensuring they perform as intended.

Enhance Incident Response Planning
Penetration testing provides insights into potential attack paths, helping you refine your incident response strategies to quickly address any breaches.
Mitigate Complex Attack Vectors
IoT ecosystems involve a complex interplay of devices, networks, and applications. Penetration testing helps identify how these elements interact and where potential security gaps exist.
Prioritize Security Investments
By understanding the most critical vulnerabilities, you can allocate resources effectively, focusing on the areas that will have the greatest impact on improving your overall security posture.
Our IoT Security Testing Services
Our IoT security testing services offer comprehensive evaluations of your IoT infrastructure. By addressing these critical areas, our IoT security testing services help you safeguard your IoT environment against potential cyber threats:

Device Security
Identifying vulnerabilities in IoT devices, including hardware and firmware analysis.
Network Security
Assessing the security of communication protocols and network architecture.
Application Security
Evaluating IoT app testing services to ensure secure interactions between devices and applications.
Compliance Checks
Ensuring your IoT ecosystem complies with industry standards and regulatory requirements.
What We Can Detect with IoT Penetration Testing
Our IoT penetration testing services are designed to uncover a wide range of vulnerabilities within your IoT ecosystem, including:
Device Firmware Vulnerabilities
Identifying weaknesses in the firmware of IoT devices that could be exploited by attackers.
Insecure Communication Protocols
Detecting flaws in the communication channels between devices and networks.
Weak Authentication and Authorization
Assessing the effectiveness of access controls to prevent unauthorized access.
Data Leakage
Identifying potential points of data leakage that could expose sensitive information.
Firmware Tampering
Detecting unauthorized modifications to device firmware that could compromise the security of the entire network.
Why Penetration Testing with Iterasec?
Iterasec application pentesting services are distinguished by our:Expert Cybersecurity Team
Our team of security experts finds juicier and more complex security vulnerabilities than other vendors.
Pragmatic Approach
We start with threat modeling and tailor our testing methodologies to suit your specific application requirements.
Delivery Quality
On-time, clear communication, proactive. Underpromise, overdeliver – that’s our motto.

In reality, there are also some further “shades” or gray, if you are not sure which one is the most optimal for you, please contact our experts to advise you on the scope
Contact usOur Expert Cybersecurity Team
Cybersecurity is an industry of constant learning. Each of our colleagues has a professional and certification development plan.
Discover All Steps How Iterasec Pentesting Service works
During our pentests we rely on the NIST, OWASP, OSSTM, CIS Benchmark and other methodologies. While employing some automated tools, we mostly perform manual expert penetration testing: such an approach proves to be the most practically valuable.
We keep clients informed in the course of the project, providing regular status updates and immediate notifications for critical findings.
- 1A kick-off meeting to agree on the scope, inputs and communication
- 2Cloud pentest (2-5 weeks, depending on the scope)
- 3The final report that highlights the identified cloud security issues
Explore our sample penetration testing service report
Please contact us, and we will send you a sample pentest report covering several applications.
Contact usWhat our clients say
Awards and Recognitions
2023
Top cybersecurity consulting company
2023
Top cybersecurity consulting company
2023
Top ponetration testing company
Related Cyber Security Services
FAQs
IoT security testing is a comprehensive evaluation process that identifies potential vulnerabilities within IoT devices, networks, and applications by simulating sophisticated cyberattacks. This testing is crucial for uncovering weaknesses that could compromise the security and functionality of IoT ecosystems.
IoT security testing is essential for businesses to protect their connected devices and sensitive data from cyber threats. By identifying and addressing vulnerabilities, companies can prevent unauthorized access, data breaches, and potential disruptions to their operations.
Key components of IoT security testing include device security assessments, network protocol analysis, application security testing, and compliance checks. These elements ensure that all aspects of your IoT infrastructure are secure and compliant with industry standards.
Contacts
Please tell us what are you looking for and we will happily support you in that. Feel free to use our contact form or contact us directly.
Thank you for submission!
We’ve received your request and will get back to you shortly. If you have any urgent questions, feel free to contact us at [email protected]