Imagine your application has broken auth mechanisms which leads to data leakage. If that’s not scary enough, imagine you’re finding out about this two weeks before the release because that’s usually when teams start running security checks. Don’t you wish they had thought about security from the beginning? It’s much better to invest in it throughout the development rather than pay for your mistakes tenfold near the end.
The good news is you can reduce design flaws by shifting security left (figuratively speaking, of course). Read on to learn more about this approach and see how threat modeling can become your first step toward it.
What is shift left security?
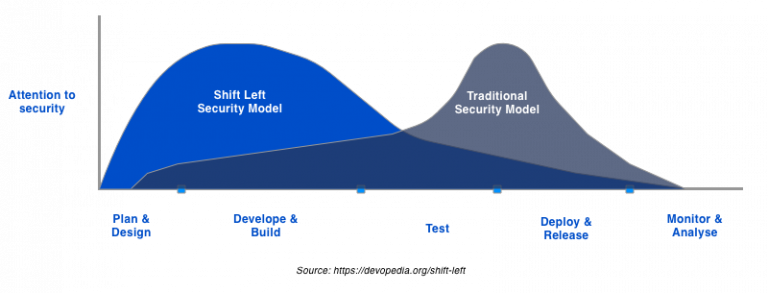
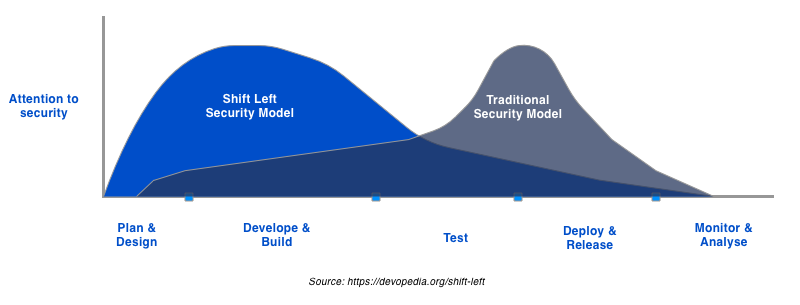
The shift left is becoming a standard requirement for secure systems design. In short, it means addressing security concerns as early as possible in the development. With this approach, dev, ops, and infosec teams collaborate closely throughout the whole software delivery lifecycle. They enact security practices early on at certain points of development.
The motivation for using the shift left approach is simple: the cost and time-to-market of addressing security only after an incident (i.e., passively) are just too much.
By contrast, shift left security is a proactive approach that offers:
- Low cost of security incidents thanks to early discovery
- More secure software by design
- Holistic security that doesn’t blindly rely on an annual penetration test.
In fact, according to the State of DevOps Report 2020, 45% of companies with full security integration can remediate critical vulnerabilities within a day.
Key Benefits of Shift Left Security
Implementing shift left security offers numerous advantages that help organizations maintain a robust cybersecurity posture while enhancing their development efficiency. Here are some of the key benefits:
Reduced Costs
By addressing security concerns early in the development cycle, the shift left security approach significantly lowers the cost associated with fixing vulnerabilities. Traditionally, discovering and rectifying security issues late in the development process or after deployment can be extraordinarily expensive. With shift left security, these costs are minimized because potential flaws are identified and mitigated before they become deeply embedded in the system. This proactive methodology not only saves money but also reduces the potential for costly security breaches.
Accelerated Time-to-Market
Shifting security left allows for faster remediation of vulnerabilities, which can speed up the overall development process. By integrating security practices into the development lifecycle from the start, teams can avoid the delays that often occur when security issues are discovered late. This seamless integration means that security does not become a bottleneck, allowing for a more streamlined and efficient path to deployment.
Enhanced Collaboration
Shift left security fosters closer collaboration between development, operations, and security teams. This integrated approach ensures that security is not an afterthought but a core component of the development process. By breaking down silos, teams can work together more effectively, sharing insights and responsibilities to create a more secure product. This collaborative environment is essential for identifying and addressing potential security issues early and comprehensively.
Improved Software Quality
By incorporating security at every stage of the development process, shift left security ensures that software is inherently more secure. This proactive approach leads to more resilient software, reducing the reliance on reactive measures such as annual penetration tests. With shift left security, security becomes a built-in feature rather than an add-on, resulting in higher quality and more reliable software.
Compliance and Risk Management
Adopting a shift left security approach helps organizations stay compliant with industry standards and regulations. By integrating security practices from the beginning, organizations can ensure they meet all necessary security requirements, thus avoiding potential fines and legal issues. Furthermore, this approach enhances risk management by identifying and addressing risks early in development, reducing the likelihood of security incidents.
Reduce costs, accelerate time-to-market, enhance collaboration, and deliver more secure and reliable software.
Increased Trust and Reputation
Organizations that consistently deliver secure products can build greater trust with their customers and stakeholders. By adopting shift left security, companies demonstrate their commitment to security and proactive risk management. This commitment protects the organization from potential breaches and enhances its reputation as a reliable and trustworthy entity in the market.
Continuous Improvement
Shift left security encourages a culture of continuous improvement. Organizations can stay ahead of emerging threats and vulnerabilities by constantly monitoring and updating security practices throughout the development lifecycle. This ongoing commitment to security ensures the organization can adapt to new challenges and maintain a strong security posture over time.
Shift left Approach: Removing the development and security friction
The shift left approach removes friction between the development and security teams. Previously, developers addressed security concerns somewhere near the end of the cycle. They’d run pentests, and the security team would deal with their results. With shifting security left, there’s no need in this traditional ping-ponging anymore.
Now dev, ops, and infosec teams are encouraged to work together on the system’s security like one big team. Naturally, this might pose some new challenges, as the team might not be aware of specific security issues. But you can solve this easily by organizing security training or separating the roles of security champions.
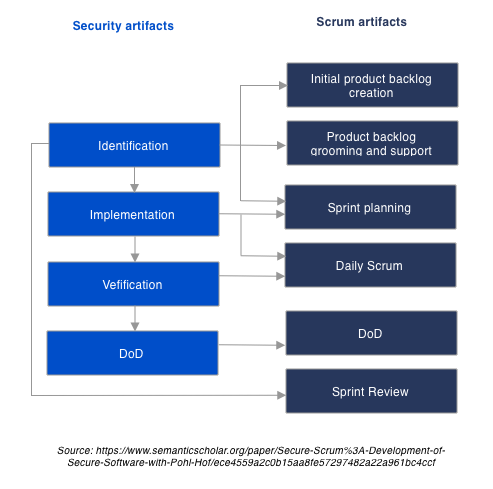
Also, the shift left approach integrates well with Agile methodologies:
As a result, security becomes an integral part of the development process and a solid product feature. From being an obstacle, it turns into a business enabler.
Shifting Security Left: What’s inside the shift left?
Let’s take a look under the hood. In general, shift left security includes:
- Architecture security review
- Threat modeling
- Secure coding practices
- Penetration tests
- Secure operations (monitoring, logs, vulnerability scans, etc.)
The shift-left approach perfectly integrates with the DevOps tooling, in particular:
- Static application security testing (SAST)
- Dynamic application security testing (DAST)
- Container scans
- Compliance scans
- Dependency scans
Moreover, these measures resonate with classic Secure SDLC frameworks – OWASP SAMM, Microsoft SDL, and others.
You have to keep in mind, though, that the shift left is not so much about specific activities as it is about the right mindset. In this approach, security becomes an indispensable part of overall quality, and every team eventually finds its own way of implementing it.
Shift Left Security Best Practices
Adopting a shift left security approach involves more than just integrating security early in the development process; it requires a strategic and holistic methodology. Here are some best practices to effectively implement shift-left security in your organization:
Threat modeling: a pillar of the shift left approach
Now, let’s talk about threat modeling, one of the first steps you can take toward shift left security. This technique helps you identify and understand various potential threats to your system. Vulnerabilities, countermeasures, attacks, and other risks — this method can reduce all of them.
Threat modeling often means answering the following questions in the technical steps:
- What are you building? You need to establish what kind of system you’ll build and define the scope of your Threat Model.
- What can go wrong? Next, you do the research and identify potential threats to your system.
- What should you do about those things that can go wrong? Identify the steps you need to take to address the issues.
- Did you do a decent analysis? Finally, double-check what you’ve done.
In a nutshell, this technique allows your team to look at the system through the hacker’s eyes. This way, they can come up with hacking/risk scenarios and anticipate the threats.
This approach offers several benefits:
- Better security design and balance. Since the team knows the weak security spots, they can invest more effort into those specifically.
- Designing a secured system from the very start. Threat modeling allows you to make the right security decisions from the get-go instead of fixing system design flaws after it’s gone live.
- A security mindset. Joint brainstorming and close collaboration on security objectives make the team more security-aligned and aware.
Incorporate Security into New App Development
Integrating security into every phase of new application development is crucial for shift left cybersecurity. It means considering security requirements during the initial planning stages, incorporating security features into the design, and performing regular security testing throughout the development cycle. By embedding security into the DNA of the application, developers can ensure that it remains robust against potential threats.
Contact our experts to get advice on the best shift left security approach for your company.
Apply Security Measures at the API Level
APIs are often the backbone of modern applications, making them a critical focus for shift left security. Implementing security controls at the API level ensures that these interfaces are protected from the outset. It means enforcing authentication and authorization, validating input data, and monitoring API traffic for suspicious activities. By integrating security at the API level, organizations can prevent common vulnerabilities such as data breaches and unauthorized access, thereby enhancing the overall security posture of their applications.
Adopt a New Shift-Left Security Approach
To successfully shift security left, organizations need to establish a comprehensive shift left security strategy. This strategy should outline clear objectives, define roles and responsibilities, and set measurable goals for integrating security into the development process. It should also include a roadmap for implementing security practices, tools, and technologies that support the shift left methodology. A well-defined strategy ensures that all teams are aligned and working towards a common goal of enhanced security.
Embed App and Container Security into the DevOps Toolchain
Integrating security into the DevOps toolchain is essential for the shift left security approach. It involves incorporating security tools and practices into every stage of the DevOps pipeline, from code commit to deployment. Teams can detect and address vulnerabilities in real-time by automating security checks and integrating them into the continuous integration/continuous deployment (CI/CD) process. Additionally, ensuring that container security is part of this integration helps protect the entire application environment.
Integrate Automated Security Testing
Automated security testing is a key component of the shift left security approach. By incorporating tools that automatically scan for vulnerabilities throughout the development process, teams can detect and address security issues early and continuously. Automated tests can be integrated into the CI/CD pipeline, providing real-time feedback and ensuring that security checks are an integral part of the development workflow. This continuous testing improves security and accelerates the development cycle.
Train Development Teams in Security Best Practices
Educating development teams on secure coding best practices is a critical aspect of shift left security. Developers must be aware of common security pitfalls and how to avoid them. Regular training sessions, workshops, and hands-on exercises can help developers understand the importance of writing secure code and staying updated on the latest security trends. By fostering a culture of security awareness, organizations can ensure that security is a shared responsibility across all teams.
Conclusion
In today’s fast-paced development landscape, integrating security early and throughout the development process is not just a best practice — it’s a necessity. Shift left security is a proactive approach that embeds security into every phase of the software development lifecycle, ensuring that vulnerabilities are identified and mitigated early on. By adopting this methodology, organizations can reduce costs, accelerate time-to-market, enhance collaboration, and deliver more secure and reliable software.
At Iterasec, we specialize in helping organizations implement strong cybersecurity strategies, including shift left security. Our expert team can guide you through every step of the process, from threat modeling to integrating security into your DevOps toolchain. Contact Iterasec today to learn how we can enhance your security posture and protect your valuable assets.